The Microsoft Build event is one of the most important events for developers and IT professionals worldwide. Each year, new innovations and technologies from the Microsoft ecosystem are presented. Although the focus is on developers, in the Microsoft Cloud world, practically all areas now seamlessly merge. Therefore, it is wrong to expect topics exclusively relevant to developers at a developer event.
I could skip most topics, as they are not really relevant to me as an integrator, and had to wade through a swamp of AI buzzwords (this year’s Book of News mentioned AI 207 times and Copilot 167 times). However, among all the sessions, there are ultimately valuable pieces of information on Azure, Security, Windows, Edge, and M365.
The GenAI hype wave already floods our feeds with almost everything from that area, so in this article, I will start with the news that does not stem from the AI field. The interesting AI features I found will follow in Part 2.
In case it’s not clear enough, I am not trying to provide a comprehensive summary of the event, but have gathered the news that I have thoughts about 😉
Security
Considering that Microsoft has prioritized security above all, no announcements in this area particularly impressed me. However, it should be noted that this new focus is still very fresh in the enterprise timeline – I am therefore looking forward to what will be announced at future events.
Windows Security
Most of the new Windows security features are theoretically very good; a better summary can be found in the dedicated security blog post.
The most important takeaway for me is that the end of NTLM is approaching. A plan for second half of 2024 was mentioned – if you have not yet audited and replaced NTLM, you can find a blog post here on what needs to be done.
A new interesting tool for managing network traffic is Zero Trust DNS. When enabled, it can enforce that only IP addresses resolved in a trusted DNS can be accessed. This makes it more difficult for malware to connect to command-and-control servers and to bypass DNS blocklists, as examples. However, it will be necessary to maintain some exceptions. Especially in times when we cannot control our clients through infrastructure level firewalls, more client-level controls are very welcome.
We will see how Zero Trust DNS is configured and what real-world experiences are gathered when the feature comes out of private preview.
Some more features based on Virtualization Based Security (VBS) were also introduced. This involves isolating highly sensitive processes from the local administrator and potential weaknesses in the host operating system by running them in their own virtual environment.
These are good features in themselves, but I have a fundamental problem with them: The architecture is extremely Windows-specific and complex. I have difficulty imagining third-party software developers tightly integrating with Microsoft security mechanisms – I believe the demand simply isn’t there. Especially considering how often alarming security practices are still found in the wild – from plaintext password databases to secrets in the code. Implementing VBS will likely – hopefully – be low on the priority list for many developers, even if there is time for security measures. These features would need to be built into libraries or handled by the operating system at runtime; otherwise, nothing will change quickly… unless…
Attestation, Trusted Signing, Smart App Control – Microsoft is increasingly taking control over which software is trusted and which is not. I assume that (among other things) these security mechanisms will increasingly become mandatory for an app to even be allowed to run on Windows. The basic principles are good, and I fully support them in the enterprise sector, as long as exceptions can still be defined. For private individuals, however, I am not a fan of one organization deciding what can be executed, especially when this organization increasingly offers its own competing products for every established software category.
Power Platform Security Hub
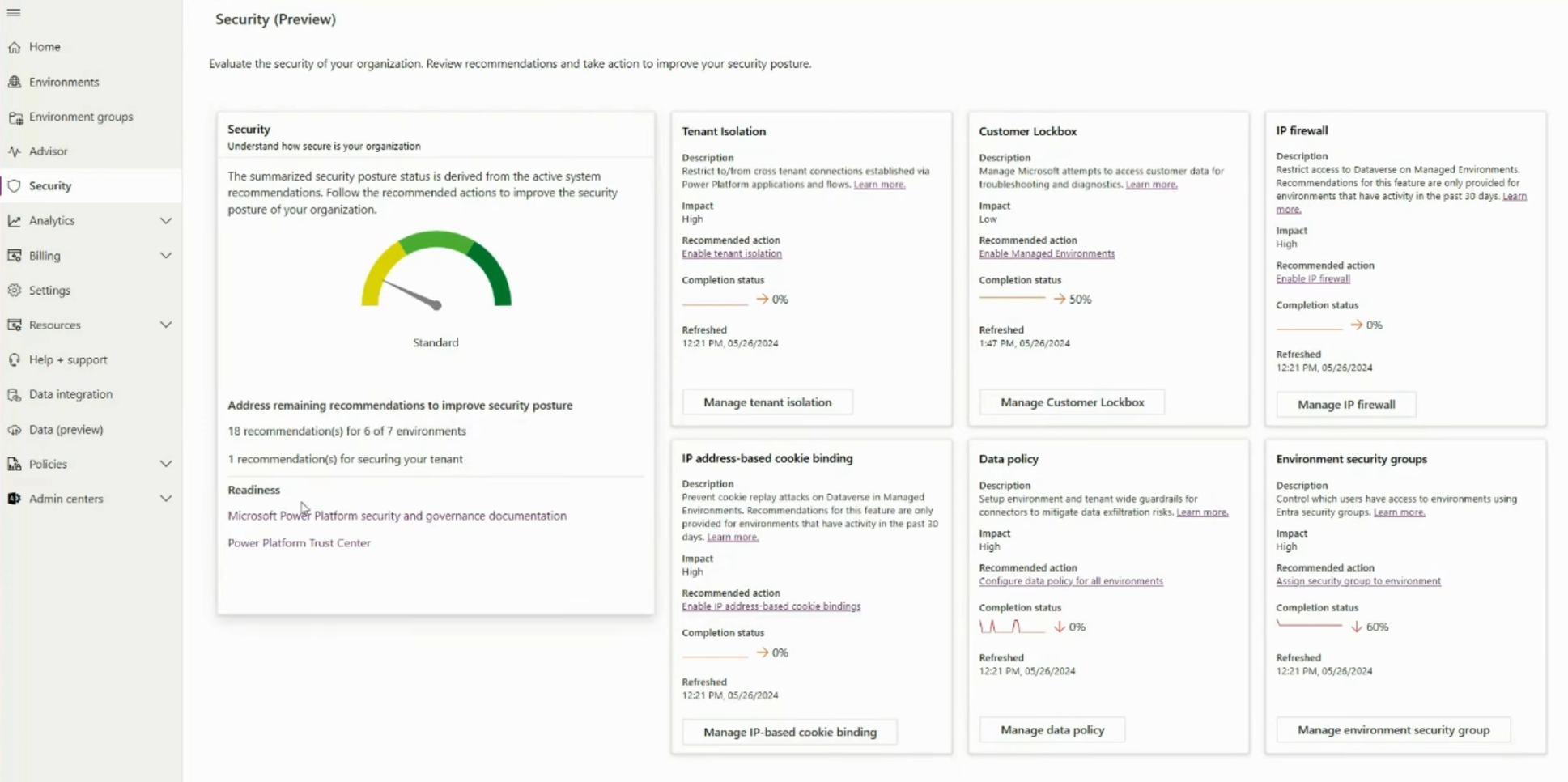
Governance and security are also crucial in the Power Platform, where business-critical processes with partially very high privileges are developed. I was therefore very pleased to see the continued development of the concept behind Secure Scores – an overview that collects easily understandable recommendations to improve security. The recommendations here look promising and will certainly be continually expanded.
Will this help organizations that have never been in the Power Platform Admin Center and perhaps even have self-service purchases enabled? Probably not – but it at least provides a good starting point if they do venture there.
My absolute highlight would have been: Support for Managed Identities. The frequency with which I see program logic operating with regular user credentials or expired secrets causing extensive troubleshooting is definitely too high. It
would also be a blessing for the creators of flows and apps if they had to worry less about credentials. I mention this because Microsoft raised hopes in March:
But it seems I will have to wait a while longer – building a custom API implementation for this seems a bit overkill.
- Here I would refer to a Microsoft doc for the Security Hub, if I could find one 🤣
- Build Power Platform Blog
Edge for Business
Anyone who has dealt with controlling data transfer in M365 on the desktop knows that previous solutions are often cumbersome or limited. With new features, Edge for Business is approaching the principle of Intune App protection policies – granular control of individual applications on external devices. I’ll just note that feature parity with Defender for Cloud App Policies without the corresponding weaknesses would be very welcome. Hopefully, I will delve deeper into this topic in the near future 😉
So here’s the short version:
-
- As already possible in some other solutions, Edge will soon make it difficult to create screenshots and screen recordings
- This feature will be available "in the coming months"
-
More control through Sensitivity Labels
- Sensitivity Labels will likely have more impact, including the upcoming screenshot prevention at some point.
- This is mentioned to be available in the next few weeks, hopefully aligning with the time I will spend on labeling
-
Defender for Cloud Apps controls through Edge
- Edge now natively respects session controls from MDCA, without having to go through the reverse proxy!
- In public preview since march, I’ll take the repetition because I’m excited to test it out
I do not accept the acronym MDA for Defender for Cloud Apps until it works outside a browser as well. 😤
Azure
Developers use infrastructure they set up themselves when following the "You Build it, You Run it" principle. Accordingly, I can understand that this event introduced several innovations for Azure resources. However, these are also highlights for me as a non-developing Azure user:
New Feature: Compute Fleet
Anyone who has tried to create multiple virtual machines in smaller Azure regions (*cough* Germany West *cough**) may have experienced a tedious search. It is often difficult to find available sizes, sometimes even for a few machines.
To simplify this process, Compute Fleets are on the way. You only need to specify two things, and Azure takes care of the rest:
- The Sizes that are eligible
- The number of servers to be reached
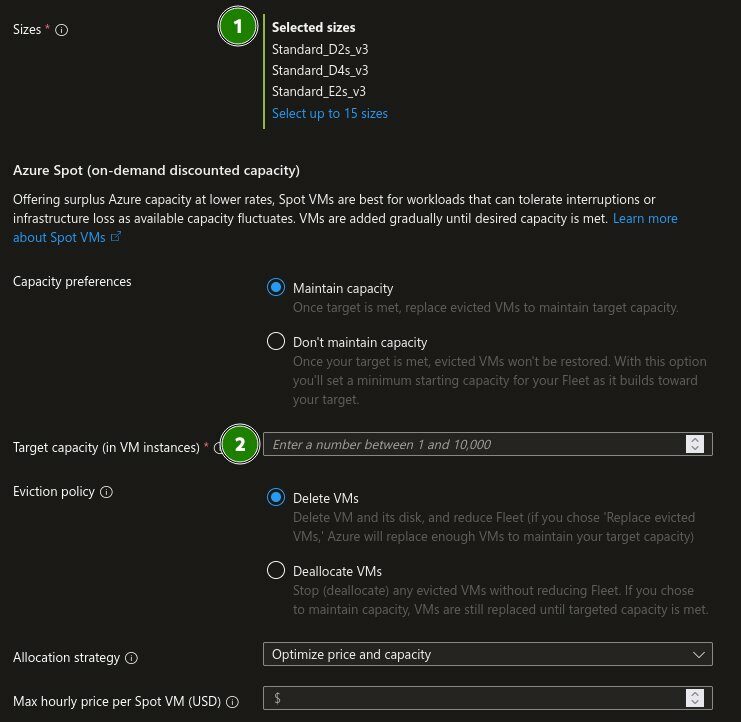
"Number of VMs" may not always be the ideal control lever.However, I am confident that granularity in how the fleet should be composed (e.g., CPU cores in the pool, RAM, etc.), will follow. Hopefully, other regions besides East and West US will become available soon as well. In the US, cost optimization will certainly be the more attractive feature, but I find the automatic search for free capacities more interesting. After all, I don’t pay the bills 😜
In case it’s not obvious enough: the last sentence is a joke. Cost optimization is of course important, just not as interesting to me.
Azure Functions: Flex Consumption und Visual Studio Code Web
First and foremost: I like Azure Functions because on-premises script hosts are prone to weak credentials in the form of service accounts and dependency conflicts between installed scripts. If you want to move away from that, Automation Accounts are still useful for simple scheduled tasks. However, for on-demand executions, Azure Functions are the right way to go for me. Webhooks without authentication in Automation Accounts are a no-go for me.
The Problem: With Azure Functions, you previously had a simplified choice between the cost-effective "Consumption Plan" and the more expensive but higher-performing "Premium Plan". The big advantage of the "Consumption Plan" is that you only pay for the executed calls. While the "Premium Plan" offers significantly more options to customize the underlying hosts, it comes with higher base costs.
The biggest disadvantage of the "Consumption Plan" is the so-called cold start, where the first response time can be significantly longer. This is because the first host needs to be started (provisioned), as the available resources are completely scaled down when not in use. In contrast, with the "Premium Plan", there can always be at least one host instance active (hot), so the function always responds immediately – but, as mentioned, this plan is usually noticeably more expensive.
Can’t we have a middle ground?
Enter "Flex Consumption": An extended Consumption Plan, where some Resources can be kept hot, like in the premium plan
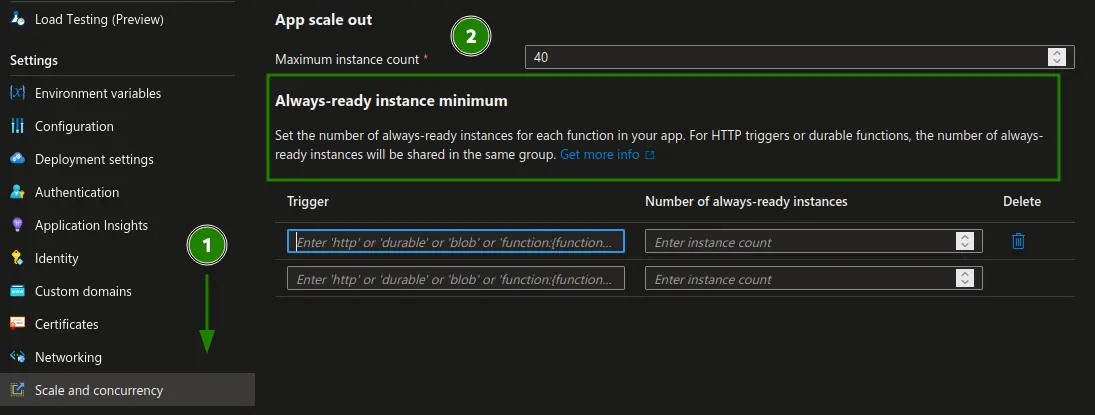
If the cold start is not an issue, there are additional reasons to switch to the new plan:
- Support for Azure VNets
- Faster scaling
- Unlimited execution times
However, I think that switching from a Premium Plan to a Consumption Plan will be more common. Those who have managed with a Consumption Plan so far will be reluctant to pay extra due to the higher GB-s price and the lower free tier 😼.
Additionally, you cannot change the plan of an existing Function. So, unless you’re willing to start a series of side-by-side migrations, this is a consideration for new Azure Functions.
Also exclusive to the Flex Consumption Plan: Integration with Visual Studio Code for the Web.
This feature is supposed to be available in PowerShell Core, Python, and .Net environments. This means you can manage Functions entirely in the browser. Although not with all the familiar extensions, in cases where establishing a connection is challenging or when you quickly want to check what is currently configured, a proper editor can make life much easier.
As of 28.05.24, creating an HTTP trigger in these environments fails for me. I also can’t find any documentation on what it should look like. 🙁
- ⚠️ Those using Infrastructure-as-Code deployments should check if the properties still match ⚠️
- Pricing Informationen (If no prices are shown, switch region)
- Flex Consumption Announcement Blog
- Flex Consumption Dokumentation
Dev Box: Better Governance
Dev Boxes are an extension of the M365 Cloud PC that includes additional tooling to quickly and project-specifically set up necessary libraries and software environments in VMs for developers. They also offer significantly higher capacities for RAM and CPU cores to meet the higher demands of developers.
In general, I believe these computers are top candidates to be moved from on-premises infrastructure to the cloud. Developer machines often have local admin rights and other security risks. The more distance you can put between these systems and the truly productive ones, the better…
From my consultant perspective, the most important innovation are new cost control options. The documentation is still a bit sparse, so I am interpreting from the text and my current understanding. More clarity will likely come in the next few weeks.
Quote from the Microsoft Dev Box Blog:
One of these new features is Dev Box hibernation, which helps control costs for dev boxes when they’re not in use. A hibernating Dev Box saves its current state and won’t accrue additional charges, making it ideal for when developers aren’t at work or are switching between multiple dev boxes for different tasks. To enable this feature at scale, admins can now set up automatic daily hibernation schedules or set Dev Box to hibernate when developers disconnect. When developers are ready to continue, they can quickly wake up their Dev Box and pick up right where they left off. We’re also introducing the ability to cap the number of dev boxes used on a per-developer, per-project basis, allowing for fine-tuning of this critical resource across the organization.
Hibernation is intended to enable faster startup times for machines without incurring billable hours. This is currently in the hands of developers, who can’t always focus on cost considerations. Therefore, a feature that provides administrative hibernation as an alternative to daily shutdowns would be very helpful. From my own experience, restarting my computer daily would significantly disrupt my workflow.
So far, I’ve only found the option to enable hibernation in the image for the Hibernate Preview:
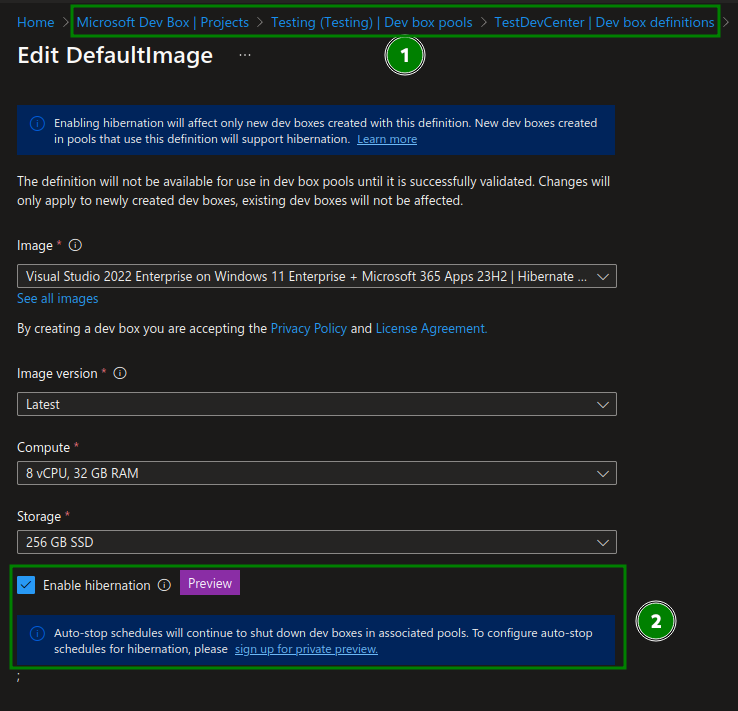
It’s not entirely clear to me where I should configure automatic hibernate and hibernate on disconnect – I assume this is still part of the Private Preview.
Also announced but not yet visible to me is the possibility to apply VM limits per developer within a project. Currently, you can only specify a project-wide cap. If certain individuals have extra requirements or need fewer machines, per-person control would likely be advantageous.
In addition to the cost-specific points, more tools should be given to team leads to build images according to their needs. Unfortunately, I haven’t seen any demos so far, only the preview sign-up. It would be very desirable for this to become a comprehensive self-service for developers instead of cumbersome coordination of requirements between departments.
Microsoft Teams
Teams has become the tool where I spend at least half of my day. It’s fascinating to see how an initially hastily assembled product that lagged behind Skype for Business has evolved into something truly impressive. Especially since it no longer consumes 80% of my RAM. The improvements just keep coming.
Faster Navigation with Slash Commands
Teams now has so many features that it can sometimes be hard to find the right place to click. This can be because you don’t remember where to go, the buttons are hidden in nested submenus or everything becomes too small. For those familiar with having one keystroke access to all common features from Confluence (as an example), will be pleased to know that the rollout begins in June. For those who aren’t familiar: I can’t explain it better than the Microsoft demo:
Meet Now in Gruppenchats
Previously, it was somewhat cumbersome to call everyone in a specific group. Messages like "Hey, I’m back, can you add me again?" were common. Now, latecomers can join group chats and participate in the conversation.
Out of protest, I briefly mention features that should not be in Teams Premium:
More granular control by the organizer over who can start recordings and transcriptions.
Prohibiting your users from sharing their screen in meetings of other organizations.
- Obvious bypass (?): The user logs out and joins the meeting anonymously.
Windows on ARM – Third Times the Charm ?
Had Microsoft never ventured into ARM before, this announcement would rank much higher. ARM chips offer significantly higher energy efficiency and are better suited for typical PC users than the now overdimensioned x86 CPUs. Apple has been demonstrating for years how impressive a well-integrated ARM architecture can be.
So why is this topic at the bottom? Let’s look at the history: As early as 2011/12, Windows 8 was supposed to unite our notebooks and smartphones – the result was… let’s say disappointing. In 2019, the Surface Pro X was supposed to herald the era of Windows on ARM. An emulator for x32 applications was supposed to bridge the gap until native apps were available. But even here, the platform was only considered “acceptable” if one used exclusively the Edge browser and the few available ARM apps.
Now, the Copilot+ PCs are supposed to make Windows on ARM mainstream. It is concerning that the "Neural Processing Unit" for AI tasks is mentioned more often than the new "Prism" x86 emulator. Despite the ARM porting efforts of major software manufacturers, the x86 alternative will remain significant in the Windows area for a long time – Microsoft cannot simply phase out x86 chips like Apple did. This significantly reduces the pressure to develop for the new platform. Could Microsoft, therefore, fail again due to the same problems that caused two previous ARM attempts to fail – the performance of non-AI apps?
I remain a sceptic and will wait for impartial reviews with bated breath – even though Microsoft has already lost me to Linux in my personal system for other reasons.
TL:DR:
So here the short summary of my Highlights. Have I forgotten anything or you have a different Opinion? Join the discussion on LinkedIn.
Security Enhancements
- NTLM deprecation is planned for the second half of 2024.
- Zero Trust DNS to enforce DNS-based security.
- Power Platform Security Hub simplifies governance and security recommendations.
- Edge for Business announces screenshot and screen recording restrictions "coming in the next few months"
Azure Innovations
- Compute Fleets facilitate the deployment of virtual machines by automatically searching for available capacities.
- Azure Functions Flex Consumption pricing plan balances cost and performance.
- Dev Box will enhance cost control with features like hibernation and limits on VMs per developer.
Microsoft Teams Updates
- Slash Commands allow quick access to features by typing.
- Meet Now in Group Chats simplifies joining and leaving spontaneous discussions.
Windows on ARM
- Performance and compatibility concerns with x86 applications remain despite new AI hardware integrations.



Comments