In this article series, I examine all places where data protection and compliance policies (hereinafter referred to as ToU – Terms of Use) can be presented to end users – preferrably with enforced acknowledgment.
In the first part, I already covered tenant-wide settings, while the second part introduced additional options within Entra ID applications.
This installment of the series now explores initial settings from the broader M365 ecosystem, which either serve directly as ToUs or can be adapted for that purpose. Although my specialty is Entra, my established criteria are well-suited to creating a comprehensive overview. 😅
I’m stepping outside my core focus area with an application whose predecessor I used to administer extensively and which I still occasionally support today: Microsoft Teams — complemented by two additional applications: Bookings, the successor to Teams Virtual Appointments, and Viva Engage (formerly Yammer) as another collaboration platform.
Teams
Microsoft Teams presents a unique challenge, as it is a platform designed to enable collaboration and interaction among a wide variety of participants. We often deal with many users from other Microsoft tenants (= guests) or even individuals who do not have a Microsoft account at all (= anonymous users).
As a reminder from Part 1: Conditional Access only applies during authentication, which means it cannot be used to enforce ToUs for anonymous participants. This presents a compliance challenge, especially when communicating with private individuals or organizations that refuse to create Microsoft accounts.
Even though some may pretend that there’s no such thing as an organization without Microsoft accounts – Business to Business (B2B) means Microsoft tenant to Microsoft tenant collaboration, after all 😉
Since anonymous users are often a critical topic, here’s an important note up front: There is currently no technical way to ensure that anonymous participants have accepted the ToU—every available solution requires organizational measures at some point.
So let’s start with the most effective option:
Webinars
In a webinar, a public "registration page" is shared, where additional information can be requested from participants. If the webinar organizer has configured the settings correctly, each participant must check a box to agree to the ToU before receiving a participation link (marked as "1" in the image).
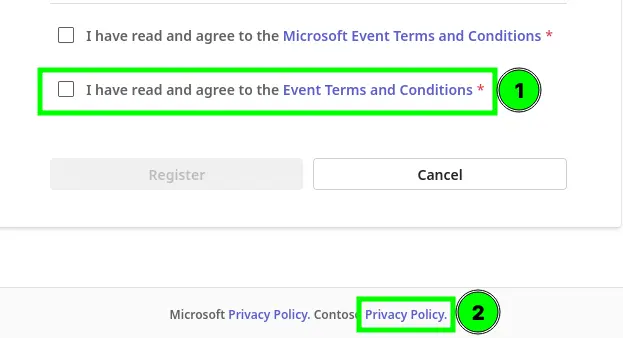
Bonus: Marker "2" again hides the tenant-wide Privacy Statement URL
To achieve this result, the webinar organizer must ensure that the settings follow the structure below every single time (or duplicate an existing, active webinar).
| Step | Description |
|---|---|
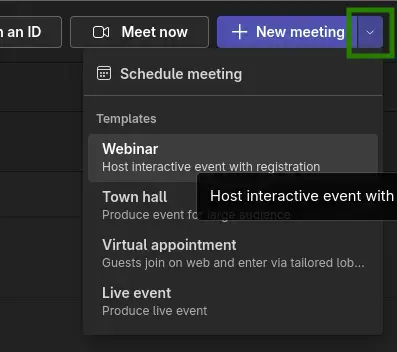 |
The organizer must create a new meeting from within the Teams app. This requires clicking the small arrow next to the "New Meeting" button and selecting "Webinar". |
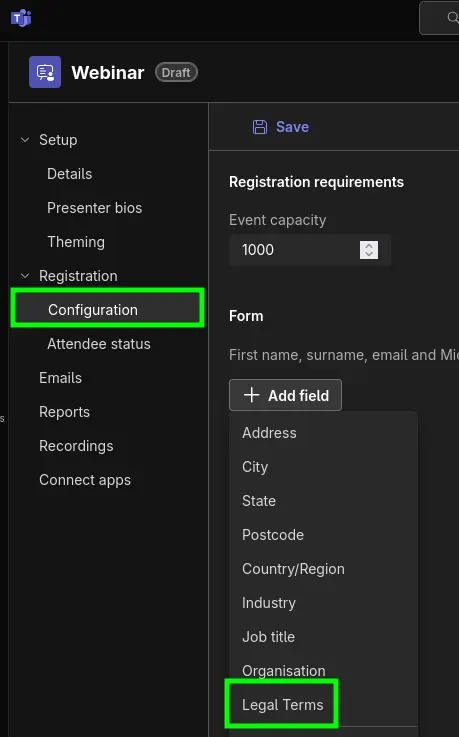 |
In the webinar settings, under "Registration > Configuration", the "Legal Terms" field must be added. This is the only field that supports URLs—all other fields accept plain text only! |
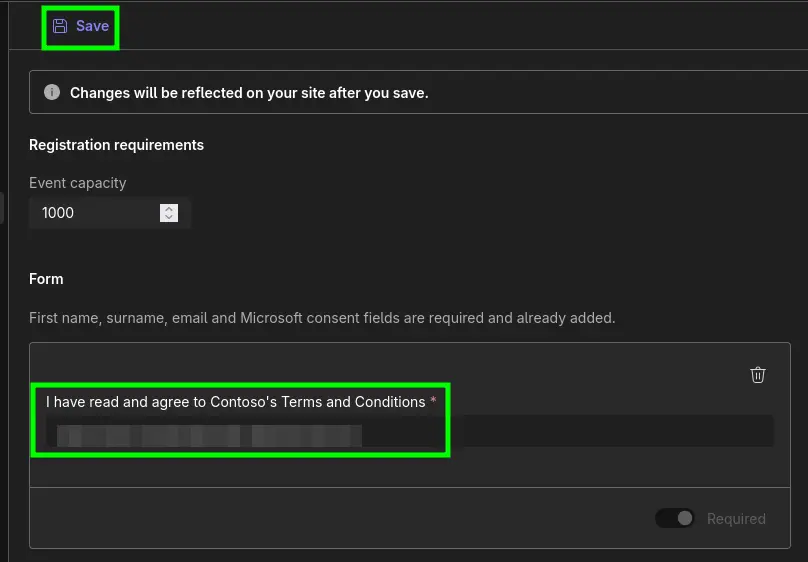 |
Finally, the URL pointing to the relevant ToU must be entered by the organizer — this must be done for each new webinar! (Don’t forget to save and publish the webinar!) |
‼️ These settings cannot be enforced administratively ‼️
Therefore, organizers must receive clear instructions and training.
Whether an anonymous user can join a webinar depends on whether the organizer’s meeting policy under "Meeting scheduling > Who can register" is set to "Everyone". Otherwise, only users from the same tenant can participate.
Meeting Invite
A significantly weaker option is customizing the meeting invite. The invitation to a Teams meeting is largely identical across all tenants, and only a few customizable elements are available. These are limited to the text in the invitation and do not include any form of enforcement or confirmation.
It’s also important to remember that meeting invites are often accepted without reading the message body, let alone any links contained within. In Outlook, users can even join a Teams meeting without ever opening the invitation.
Nevertheless, there are two places where important information for participants, including ToU, can be placed: the "Footer" and the "Privacy and Security URL", both found in the Meeting Settings of the Teams Admin Center.
⚠️ The invitation customization applies tenant-wide — this method is therefore unsuitable for department- or team-specific notices.
| Admin Center Setting | Result |
|---|---|
 |
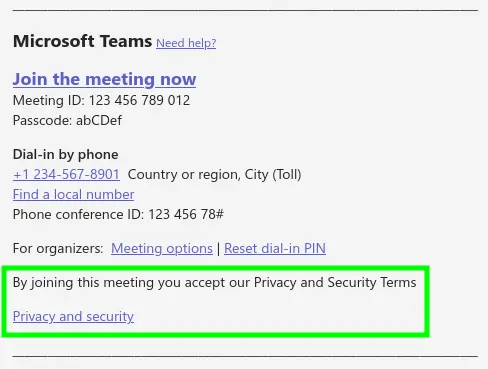 |
Reminder: When joining a Teams meeting, the tenant-wide privacy URL is displayed under "Privacy and cookies".
Handling Anonymous Users
Why anonymous users are a problem
As should now be clear: anonymous users do not provide any information to our tenant — they simply enter a freely chosen name and join the meeting to which they were invited. That’s why Teams meetings display the status "unverified" next to their names.
This results in a significant loss of control and governance capabilities, especially the inability to enforce Conditional Access ToUs.
⚠️ Note: There are many granular configurations for anonymous users, guests, and B2B governance — these go beyond the scope of this article, which focuses strictly on ToU-relevant settings.
Clearly Separating Webinars from Regular Meetings
The good news: if you need webinars but want to prevent anonymous users from joining regular Teams meetings, you can already exclude a large portion of otherwise "unverified" participants.
Webinars are controlled via the Meeting Policy setting “Meeting scheduling > Who can register.” This setting is managed separately from the general configuration for anonymous users.
When should you block anonymous users?
Ask yourself the following questions:
- Do my employees interact almost exclusively with known organizations?
- Are meetings with unknown organizations/individuals primarily conducted via webinars?
- Can exceptions be handled through targeted policies?
➡️ If the answer is mostly “Yes,” anonymous user participation should be disabled.
Used Meeting Policies
In the global Meeting Policy, anonymous participation can be disabled via:
“Meeting join & lobby > Anonymous users can join a meeting unverified”
Since this is a Meeting Policy, you can later assign an exception policy to specific organizers who need to work with anonymous users.
Disabling anonymous access often quickly reveals where B2B tenant configurations are missing or where external users haven’t been invited as guests. However, guest account setup and governance go beyond this article’s scope.
A preview: You’ll find many organizations that enforce strict B2B trust requirements.
📌 Important Notes on Teams Policies
- Each user can only have one policy of each type active at a time
- The organizer’s policy is the one that applies, not the participant’s
- Policy changes may take up to 24 hours to become active
- Signing out and back in can help accelerate policy application
Here’s Microsoft’s documentation on anonymous users in meetings
If collaboration with anonymous users is limited to a specific area, the next ToU tool is often useful: in many cases, these Teams meetings are linked to bookable services.
Bookings
Microsoft Bookings is Microsoft’s solution for offering services directly via one’s Exchange calendar. There are two variants: Shared booking pages (classic) and Personal booking pages (new), the latter having evolved from heavy use of shared booking pages for individual calendar availability.
For ToU purposes, the classic version is of particular interest, as it offers significantly more customization options for the booking page. While custom text fields can be configured, they are not suitable for ToUs, as neither URLs nor file uploads are supported.
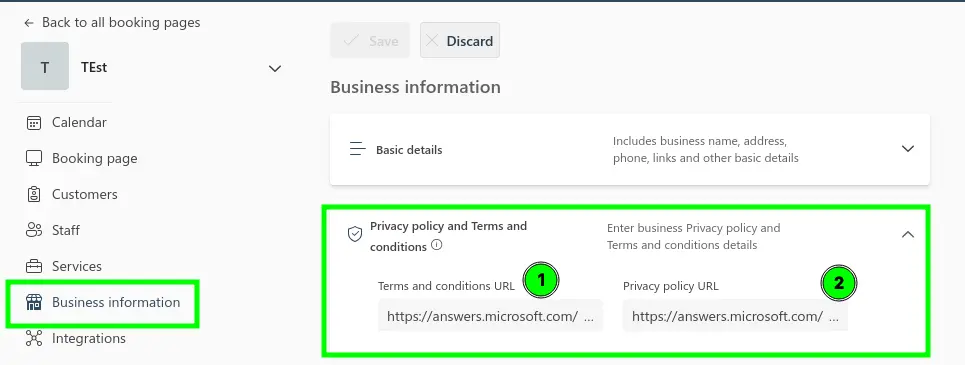
First, a booking page administrator must enter the relevant ToU details in the Business Information section:
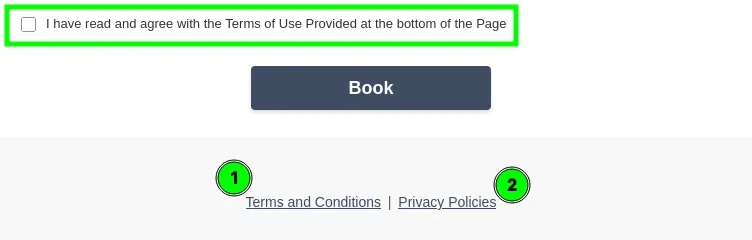
Next, consent must be activated — ideally with a clear message. (If your ToU are very short, they can be entered directly — URLs do not work!)

The result: a booking is only possible if the user agrees to the ToU.
Important: There is no technical safeguard preventing the owner of the Bookings page from directly sending invitations to clients or participants — proper training is therefore essential.
‼️ Note: Teams meetings created via Bookings are subject to standard user policies. The organizer of the generated meeting is always the person who created the Bookings page. Their meeting policy must therefore allow anonymous users!
To complete the overview of collaboration applications, let’s now explore the options available in Viva Engage:
Viva Engage (Yammer)
Viva Engage (formerly Yammer) offers a particularly strong method for enforcing Terms of Use: access to the platform can be fully blocked until users accept a custom ToU.
This feature is especially useful for:
- Behavior guidelines (“Terms of Conduct”) for platform usage
- Notices on data privacy, IT usage, or external codes of conduct
Configuring the Usage Policy
-
Open the Admin Center:
https://www.yammer.com/[TENANTNAME.onmicrosoft.com]/admin/usage_policy -
Enable mandatory acceptance of the ToU
(optional: display a permanent reminder message) -
Design the text in HTML format
- Links to privacy statements using
<a href="">are supported - You can freely combine conduct and compliance content
- Links to privacy statements using

What Does the User See?
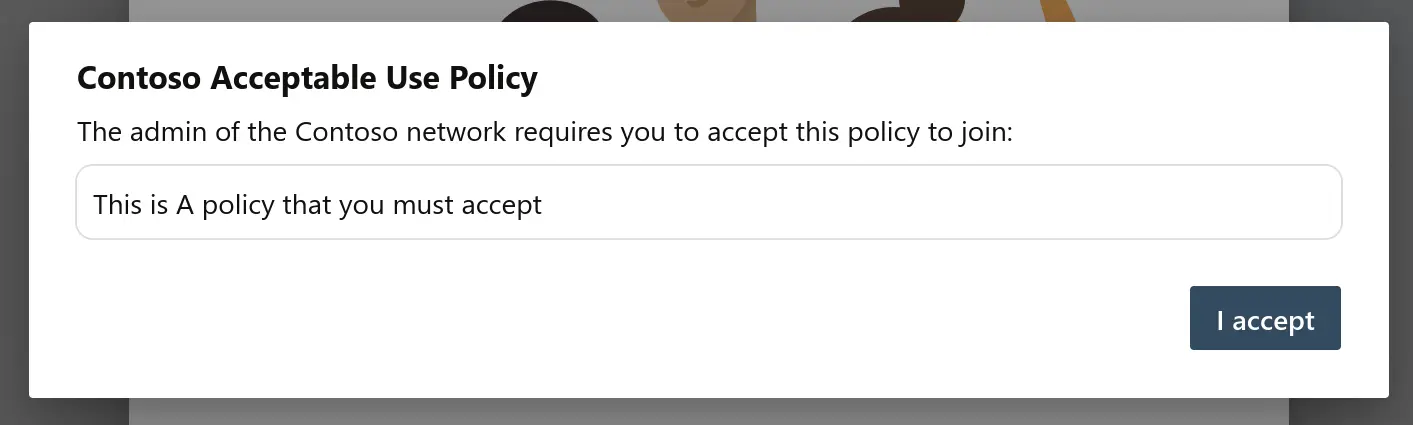
- Upon first login (and whenever the ToU is updated), the full policy text is shown — acceptance is mandatory:
- The so-called “Sidebar Reminder” remains permanently visible and opens the full policy when clicked:
⚠️ Note: Unlike Conditional Access, there is no visibility into which users have accepted the ToU.
However, since acceptance is enforced and the reminder is persistent, compliance is reliably ensured in practice.
Summary
In this part of the series, we explored the following options for presenting and confirming Terms of Use within M365:
| Setting | Affects User Types | Where Displayed | Explicit Confirmation | "Content Type" |
|---|---|---|---|---|
| Teams Webinar | All * | During registration * | ✅ * | URL |
| Teams Meeting Invite | All | In the meeting invitation | ❌ | Plain text + URL |
| Bookings (Shared) | All ** | During appointment booking | ✅ *** | Plain text + URL |
| Viva Engage | All | At first login and upon changes | ✅ | HTML |
* If the organizer properly configures the webinar
** If users are consistently invited via the Bookings page
*** Considered explicit consent at the discretion of the compliance department
I’ve stopped trying to predict when I’ll be finished — more Microsoft 365 applications with potential ToU touchpoints will follow in the next part of this series 😅
If there’s something you know that I could include, or if you have a particular interest, feel free to drop a comment or connect with me on LinkedIn!

Comments